Mon - Sat 8:00 - 17:00, Sun - Closed
Email: info@theezenergy.com


24/7 Service
+44 7961 391 786
Visit our place
Norfolk Square London W2 IRT
Automotive Work
- Home
- Certified Ethical Hacker

Certified Ethical Hacker
Creators of Certified Ethical Hacker comes the new evolved version 13 with added AI capabilities. Structured across 20 learning modules covering over 550 attack techniques, CEH provides you with the core knowledge you need to thrive as a cybersecurity professional • Benefit from Flexible learning options • Earn a globally recognized certificate • Get practical learning with 221 hands on labs
The Certified Ethical Hacker (CEH) certification is important for several reasons, especially in the field of cybersecurity: Industry Recognition: CEH is globally recognized and respected. It validates your skills in ethical hacking and cybersecurity. Career Opportunities: It opens doors to roles like penetration tester, security analyst, or cybersecurity consultant. Legal Hacking Skills: CEH teaches how to think like a hacker—legally. This helps in identifying and fixing security vulnerabilities before malicious hackers exploit them. Updated Knowledge: The certification ensures you're trained on the latest tools, techniques, and attack vectors. Compliance & Regulations: Many companies require CEH-certified professionals for compliance with standards like ISO 27001, PCI-DSS, and others. Boosts Credibility: It adds credibility to your resume and increases your chances of promotions or salary hikes.
Ethical Hacking Phases • Five Phases of Ethical Hacking o Phase 1 – Reconnaissance o Phase 2 – Scanning o Phase 3 – Gaming Access o Phase 4 – Maintaining Access o Phase 5 – Clearing Tracks
Best Ethical Hacking Tools & Software for Hackers • Netsparker Ethical Hacking Tool • Acunetix Ethical Hacking Tool • Traceroute NG Ethical Hacking Program • SolarWinds Security Event Manager Ethical Hacking Tool • Burp Suite Ethical Hacking Tool
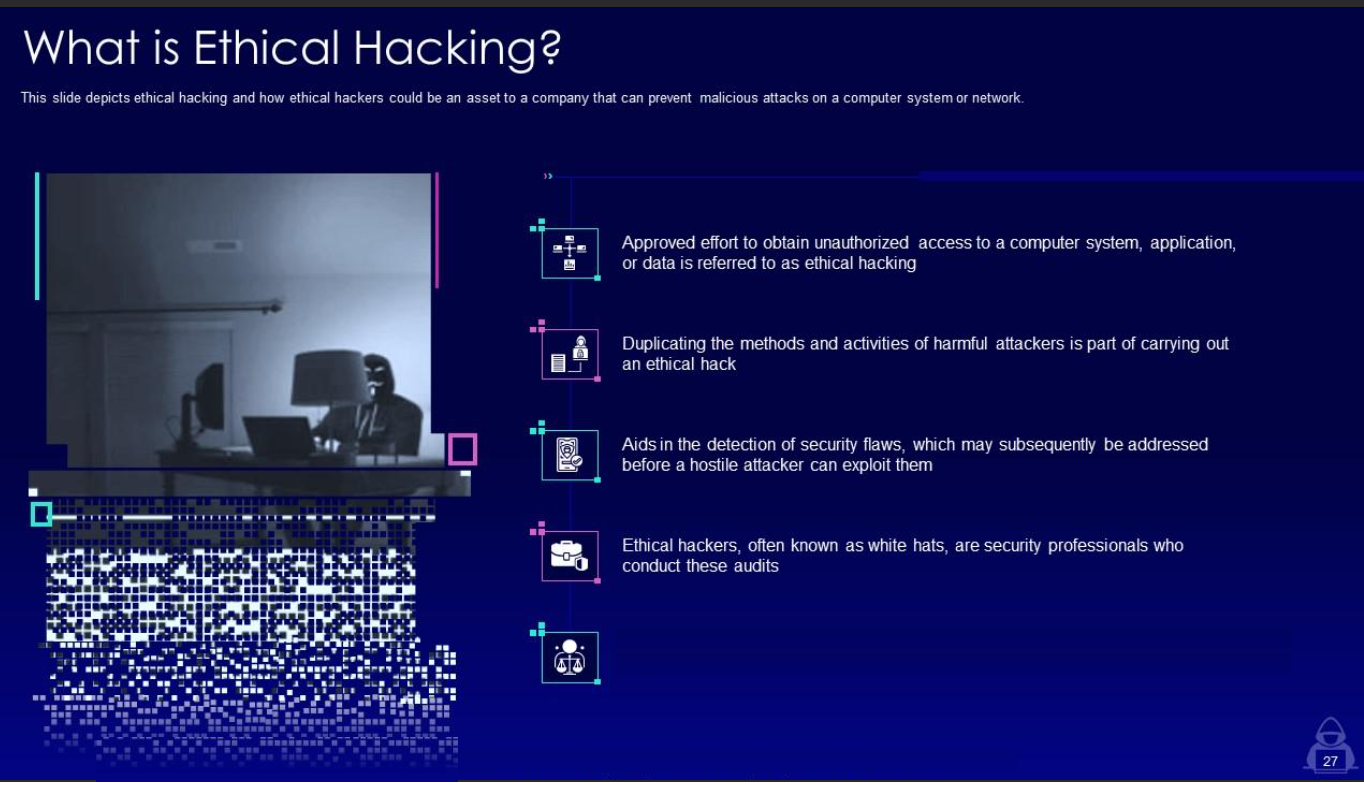
Comparison Between Different Hackers and Ethical Hacking and Penetration Testing • White Hat Hacker Vs Black Hat Hacker • How are Ethical Hackers Different than Malicious Hackers • Ethical Hacking Vs Penetration Testing
Techniques We used in Hacking • What is Phishing Attack? o Types of Phishing Attack o Security Measures to Prevent Phishing • Domain Name System (DNS) Spoofing • Cookie Theft Technique of Hacking • Cross-site Scripting Technique of Hacking (XSS) • SQL Injection (SQLi) Technique of Hacking • Techniques Used in Ethical Hacking
Pellentesque vel dolor consectetur, ate eros vitae, molestie felis. Vivamus orna reague lorem at vulputate leo.
Masum Billa
Exclusive at UX/UI
Pellentesque vel dolor consectetur, ate eros vitae, molestie felis. Vivamus orna reague lorem at vulputate leo.
Masum Billa
Exclusive at UX/UI
Pellentesque vel dolor consectetur, ate eros vitae, molestie felis. Vivamus orna reague lorem at vulputate leo.
Masum Billa
Exclusive at UX/UI

